
Executive Summary
This report uncovers critical security vulnerabilities in the voting systems used in various states across the United States. Through comprehensive analysis, significant issues were identified, particularly with the use of hard-coded passwords embedded in the source code. These vulnerabilities raise serious concerns about the overall security and integrity of these systems.
Key findings include:
- Hard-Coded Passwords: The discovery of a hard-coded password that has remained unchanged since at least 2010. This password is embedded directly in multiple points in the source code, making it easily exploitable by anyone with access to the code.
- High-Level Access Vulnerabilities: User accounts with high-level administrative privileges, such as MRE Super Admin, are inadequately protected. These accounts likely have extensive access rights, making their compromise particularly dangerous.
- Widespread Use of Global Passwords: The same global password is used across multiple voting systems in different states, including Georgia, Arizona, New Mexico, and Michigan. This uniformity creates a single point of failure, increasing the risk of widespread unauthorized access.
- Weak Password Management Practices: Passwords are not unique per user within counties, meaning multiple users share the same password. This further compromises security, making it easier for unauthorized users to gain access.
- Lack of Salting in Hashing: While some passwords are hashed, they are not salted. Salting adds a unique, random value to each password before hashing, ensuring that even identical passwords have different hashes. The absence of salting allows for reverse lookups of hashed passwords, significantly weakening security.
The data and insights in this report are heavily informed by the findings of Cyber Ninjas, a group of analysts who conducted a thorough analysis of the voting systems in Antrim County, Michigan. Their report highlighted numerous security issues, including the hard-coded passwords and lack of proper encryption practices.
This report underscores the urgent need for enhanced security protocols to safeguard our voting systems. Recommendations include:
- Eliminating hard-coded passwords from source code.
- Implementing proper salting techniques in password hashing.
- Ensuring unique passwords for each user within all systems.
- Conducting regular security audits to identify and rectify vulnerabilities.
By addressing these issues, we can significantly improve the security and integrity of our election infrastructure, ensuring the protection of sensitive election data and maintaining public trust in the electoral process.
Introduction
In this report, we delve into the critical security vulnerabilities found within the voting systems used across several states in the United States. Through comprehensive analysis and investigations, many organizations have uncovered significant issues with the passwords embedded in these systems, which raises serious concerns about their security and integrity.
How long have these vulnerabilities existed, and just how secure are these systems supposed to be? These questions are crucial as we examine the evidence and implications of the flawed security measures that have been in place for over a decade. From hard-coded passwords to the lack of proper encryption techniques, my findings reveal a troubling landscape of lax security practices that could potentially, or has already, compromised the integrity of our electoral process.
This report aims to shed light on these vulnerabilities, demonstrate the potential risks associated with them, and underscore the urgent need for enhanced security protocols to safeguard our voting systems. By understanding the depth of these issues, we can advocate for the necessary changes to ensure the protection and reliability of our election infrastructure.
Cyber Ninjas
A significant portion of the data and insights in this report comes from the findings of a group of analysts known as Cyber Ninjas. Cyber Ninjas conducted a thorough analysis of the voting systems used in Antrim County, Michigan's 2020 presidential election. Their comprehensive report highlighted numerous security issues, providing a detailed examination of the vulnerabilities inherent in these systems. Their work has been instrumental in uncovering flaws such as hard-coded passwords and inadequate encryption practices, which have raised alarms about the overall security of the election infrastructure. By leveraging their detailed findings, this report builds on the Cyber Ninjas' analysis to further explore the widespread nature of these vulnerabilities and advocate for necessary security improvements.
In their report, they discussed a security deficiency dating back to August 2010. According to this Deficiency Report, hard-coded passwords and cryptographic keys were identified as a problem.
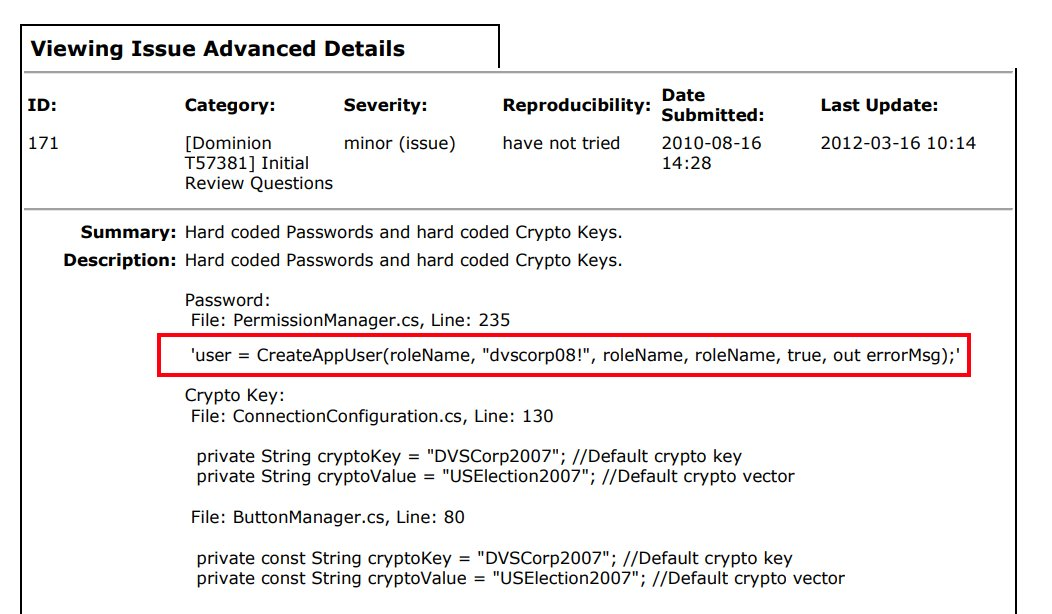
In this code snippet, called 'Permission Manager', the code created a new record in the AppUser database table with a hard coded password.
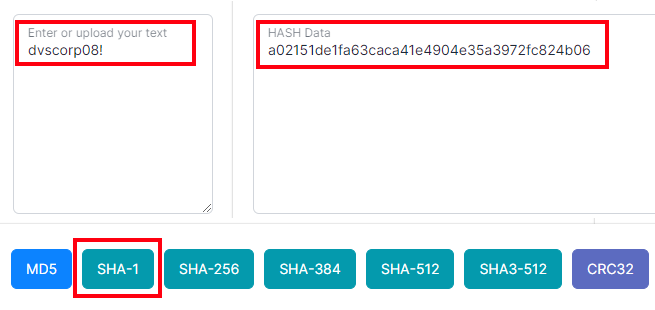
dvscorp08!
This is a significant issue. The password dvscorp08! was hard-coded directly into the source files at least 14 years ago. One would assume that this problem has been fixed by now, or at the very least, the password has been changed. Unfortunately, that assumption would be incorrect.
Hashing a Password
During an Open Records Request by Garland Favorito's group, VoterGA, four of the Georgia counties released backups of their voting system database. This database is a Microsoft SQL Server database with no security enabled, and can easily be opened with Microsoft's SQL Server Management Studio.
I was able to query the database table 'AppUser' and see some user names and passwords password stored for various users.
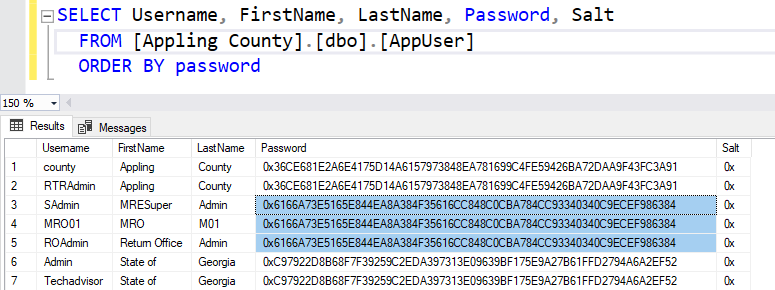
These globally used passwords are stored in this database table for the following usernames:
- SAdmin - MRE Super Admin
- MRO01 - MRO M01
- ROAdmin - Return Office Admin
6166a73e5165e844ea8a384f35616cc848c0cba784cc93340340c9ecef986384
While I am unsure of the exact abilities these users have, the name MRE Super Admin suggests a significant level of access. This title typically implies full administrative rights, which could include the ability to modify or delete data, create or disable user accounts, and access sensitive information. This level of access in the hands of an unauthorized user could compromise the entire system.
The other user accounts, with titles like Super Admin and Return Office Admin, likely has high-level privileges. The uniformity of these credentials across various systems means that once an attacker knows the password for one system, they potentially have access to all systems using the same setup. This significantly increases the risk of a widespread breach.
One thing we notice is that the stored password isn't in plain text, but instead is hashed. Hashing is a process that converts a password into a fixed-length string of characters, which appears random. It's a common and useful step for securing passwords if done properly. However, while hashing makes it difficult to reverse-engineer the password, the lack of 'salting' weakens this security measure. Salting adds a unique, random value to each password before hashing, ensuring that even identical passwords have different hashes. The '0x' in the salt column indicates that they used the default open hashing method without adding any salt.
To demonstrate this, let's hash the password dvscorp08! that we found in the Deficiency Report. There are many online password hashers available; for this test, I used Online Web Toolkit's hash generator. Once you hash the password, it turns into a complex string like this:
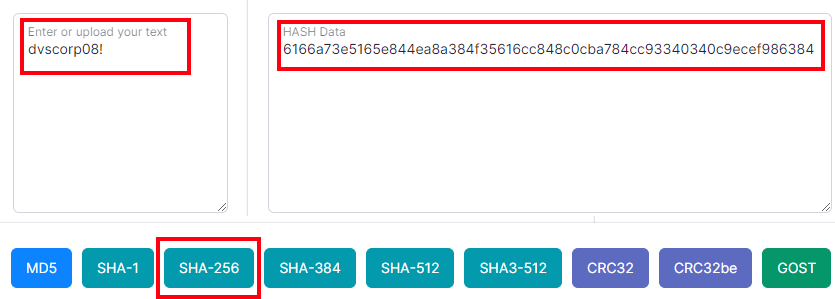
6166a73e5165e844ea8a384f35616cc848c0cba784cc93340340c9ecef986384
That's the exact same value that is stored in the AppUser database!
That means that we now know the admin passwords to at least 3 accounts for this machine.
Reversing the Hash
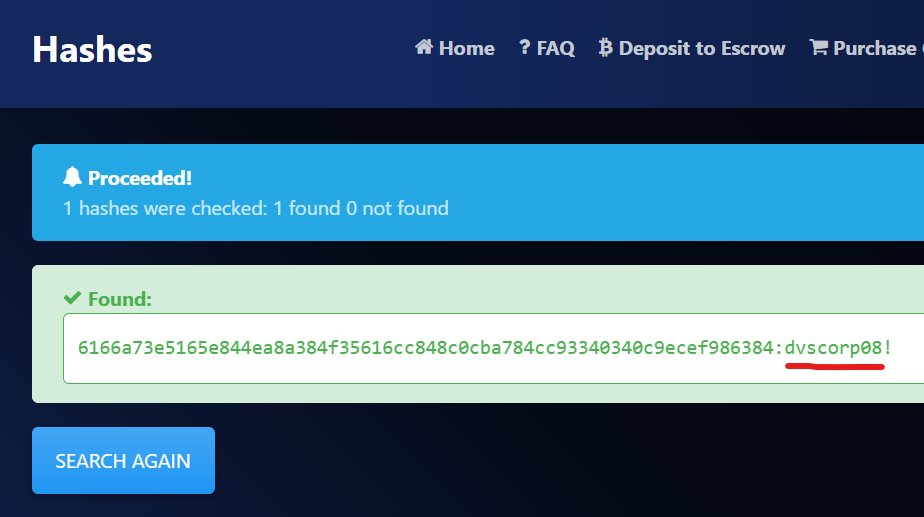
Using a one-way hash is a good practice, but the lack of salt means the hash remains the same every time. Without a salt, reverse lookups of the hash can easily reveal the original password.
Cyber Ninjas demonstrated this by using Hashes.com to restore the hashed password back to its original form. They were able to prove the hashing method is faulty and revealed the password dvscorp08!. This highlights the importance of salting hashed passwords to prevent reverse lookups and maintain security.
Additionally, passwords in the database should never be stored in a way that allows them to be easily decrypted. Salting strengthens the hashing process by making each hash unique, thus significantly enhancing password security.
Try it out for yourself at Hashes.com
Who uses this password?
This password is embedded in the source code, and its hash can be easily reversed. But where is it used? Frankly, it could be in every DVS system that has been in operation for years.
I have found this password being used in at least seven database systems across Georgia, Arizona, and New Mexico. Cyber Ninjas also discovered the use of this password in Antrim County, Michigan.
The presence of this password in multiple systems indicates a widespread security issue. These systems likely share a common setup, making them vulnerable to similar attacks. When a password is hard-coded and not properly protected, it can be exploited by anyone who gains access to the source code or the hashed password.
The continued use of these hard-coded passwords without proper security measures, such as salting and regularly updating passwords, creates a major vulnerability. It highlights the need for stringent security practices, including unique passwords for each system, regular updates to security protocols, and thorough audits to identify and mitigate potential risks.
More Counties
Below are two more counties where the same exact globally used password is available on multiple machines throughout the country. This widespread availability underscores the severity of the security issue. Additionally, while the other passwords in these systems are unique per county, they are not unique per user. At least two users sharing the same password further indicates a weak password management system.
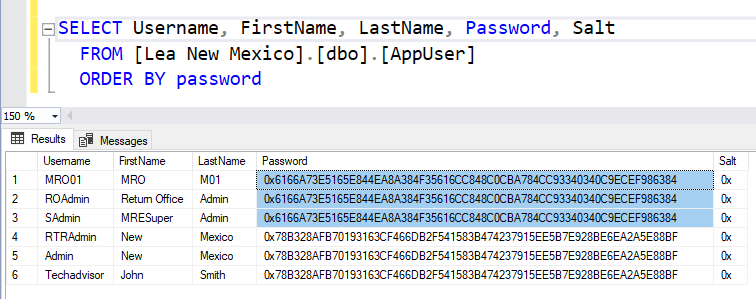
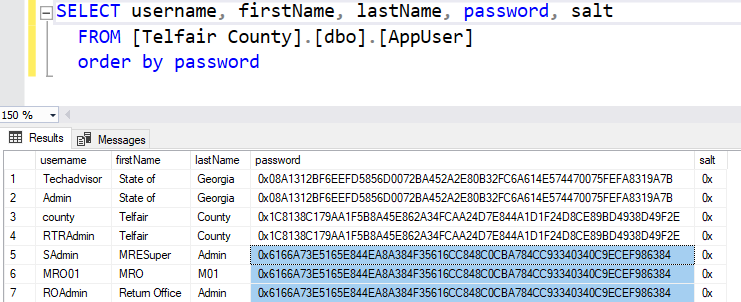
The use of a global password across different machines and the repetition of passwords among users within the same county highlights a critical weakness in the password management system. Ideally, each user should have a unique password to ensure that if one account is compromised, it does not jeopardize others. Furthermore, the presence of a globally used password that can be used across multiple systems creates a single point of failure, making it easier for an attacker to gain widespread access.
This weak password management system not only increases the risk of unauthorized access but also makes it difficult to track and manage potential security breaches. Each user having a unique password is a fundamental security practice that enhances accountability and reduces the risk of widespread breaches. The continued reliance on global and non-unique passwords reveals a need for a comprehensive overhaul of the current security practices to protect sensitive election data effectively.
More hard coding of the global password
The storage of the password can also be seen hard coded into other parts of the code as well. Cyber Ninjas were able to find more hard coded password in other areas. They used a common program 'grep' to search the binary code for the word 'password' and this is what they discovered.
In the file DVS.DemocracySuite.DatabaseService.dll
- username="SAdmin" password="YWanPlFl6ETqijhPNWFsyEjAy6eEzJM0A0DJ7O+YY4Q="
- username="MRO01" password="YWanPlFl6ETqijhPNWFsyEjAy6eEzJM0A0DJ7O+YY4Q="
- username="ROAdmin" password="YWanPlFl6ETqijhPNWFsyEjAy6eEzJM0A0DJ7O+YY4Q="
- username="Techadvisor" password="YWanPlFl6ETqijhPNWFsyEjAy6eEzJM0A0DJ7O+YY4Q="
- username="Admin" password="oCFR3h+mPKykHkkE41o5cvyCSwY="
If those user names might seem a bit familiar, it's because they are the user names that are stored in the database for the users. This is probably the source of the default database tables and where the keys are coming from
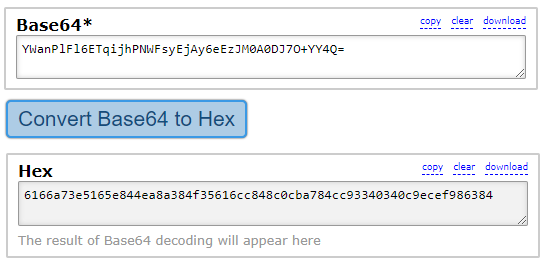
The password will look a bit different, but it's only because of how it was stored in the program. This code
YWanPlFl6ETqijhPNWFsyEjAy6eEzJM0A0DJ7O+YY4Q=
is known as a base64 character string and is a common way to store binary values inside code by using standard letters. If you copy this code to a base64 online decoder, you will get the original hash code. Which means that the global password is used here too.
6166a73e5165e844ea8a384f35616cc848c0cba784cc93340340c9ecef986384
Older Hashes
Of the many passwords that were found by Cyber Ninjas, one of them stands out as being a little different.
- username="Admin" password="oCFR3h+mPKykHkkE41o5cvyCSwY="
oCFR3h+mPKykHkkE41o5cvyCSwY=
We will take it a few steps, by first converting it from Base64 to Hex
a02151de1fa63caca41e4904e35a3972fc824b06
Notice that this hash is smaller than the original one. The previous one used a hash algorithm called SHA-256. This is apparently an older password that used a hash algorithm known as SHA-1.
Return to the Hash Generation Website, enter in the global password and click on the 'SHA-1' button this time. You'll see that the hash is the same, proving that this was just a different hashing algorithm.
Summary
This article highlights significant security vulnerabilities in the voting systems used in various states across the United States. One of the most alarming issues is the use of a hard-coded globally used password embedded in the source code, which has remained unchanged since at least 2010. This password has been discovered in multiple database systems across Georgia, Arizona, and New Mexico, and even in Antrim County, Michigan, as revealed by the Cyber Ninjas.
The practice of hard-coding passwords and failing to use proper security measures, such as salting hashed passwords, severely compromises the security of these systems. The lack of unique passwords for individual users within counties further exacerbates the problem, creating a weak password management system that makes it easier for unauthorized access to occur.
Examples provided in this report demonstrate the widespread availability of the global password across different machines and the repetition of passwords among users. This not only increases the risk of breaches but also complicates the tracking and management of such incidents.
The presence of user accounts with high-level administrative privileges, such as 'MRE Super Admin', without adequate security protocols in place, poses a significant threat to the integrity of the voting systems. The continued reliance on outdated and insecure password practices underscores the urgent need for a comprehensive overhaul of the current security measures.
To ensure the integrity and security of election data, it is imperative to implement robust security practices, including unique passwords for each user, regular updates to security protocols, thorough audits, and the elimination of hard-coded passwords in the source code. Only through these measures can we protect our voting systems from potential vulnerabilities and maintain the trust and confidence of the public in the electoral process.
References & Acknowledgement
Thanks to Cyber Ninjas and Dr. J. Alex Halderman for their amazing work in highlighting their discoveries.
Antrim County, Michigan, Election Management System Application Security Analysis - by Cyber Ninjas (040921)
Antrim-County-Michigan-Election-Management-System-Application-Security-Analysis-by-Cyber-Ninjas-040921WYLE TEST REPORT NO. T57381-01 APPENDIX A.11 DEFICIENCY REPORT
https://www.eac.gov/sites/default/files/voting_system/files/Deficiency%20Report.pdfAnalysis of the Antrim County, Michigan November 2020 Election Incident
https://www.michigan.gov/sos/-/media/Project/Websites/sos/30lawens/Antrim.pdf


 English
English


